What to Look For in Employee Monitoring Software
Computer monitoring software is a must-have for businesses of all sizes. Not only will monitoring software watch network activity, but it will also provide useful tools for insider threat detection, productivity monitoring, and act as an additional safeguard against potential risks.
Since monitoring software is a vital security measure, you want to be sure that you purchase an effective tracking tool with features that best suit your needs.
Here are 15 features that should be in your employee monitoring software.
Live Remote Desktop View
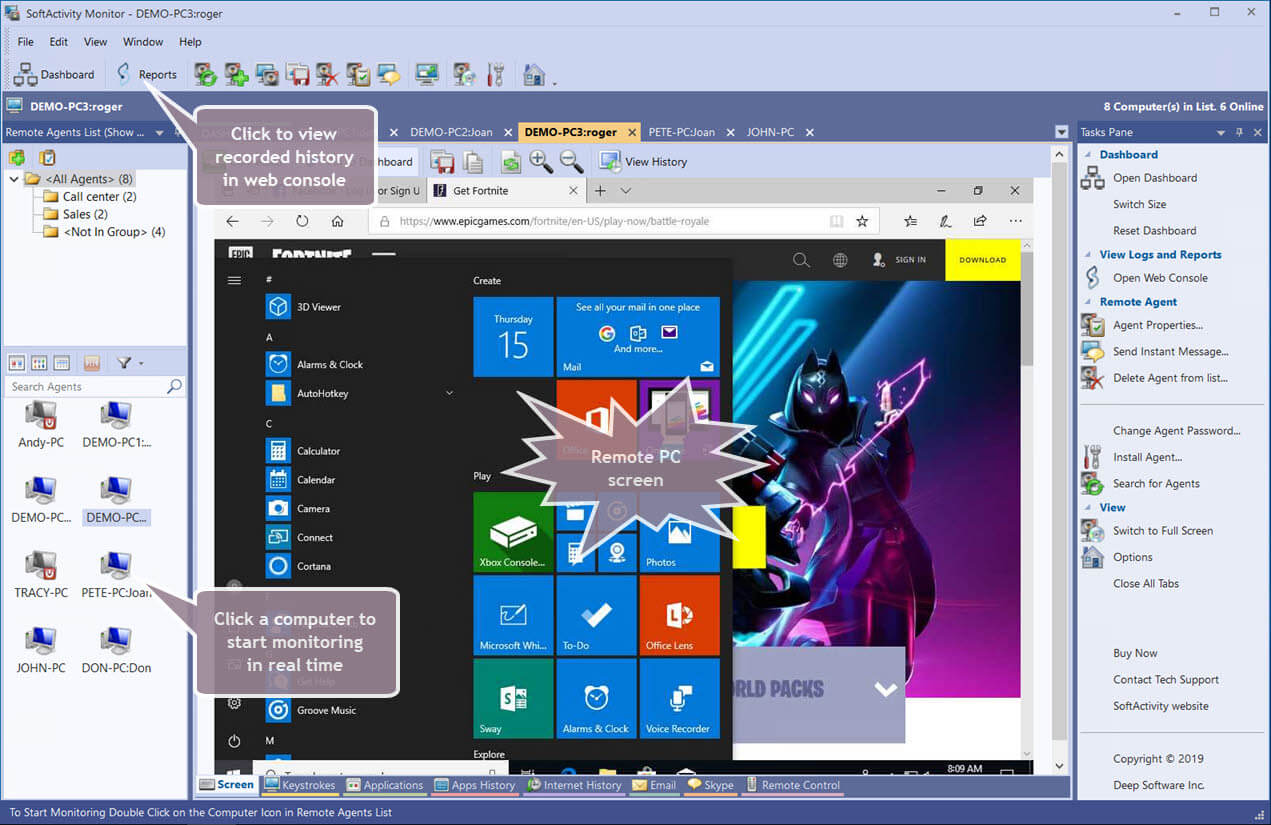
If you are monitoring a large network or multiple networks, it can be time-consuming to go through hours of user reports. Some software will allow the admin console to silently remote desktop in for live employee tracking. You can view multiple users on one screen in real-time to boost productivity during work hours.
Real-Time Tracking
A real-time tracker records, in stealth mode, the length of time an application, webpage, chat or email was accessed. It will generate a Top Programs report so you can identify how long an employee spends performing certain tasks. This is a crucial feature if your company has a lot of employees working remotely.
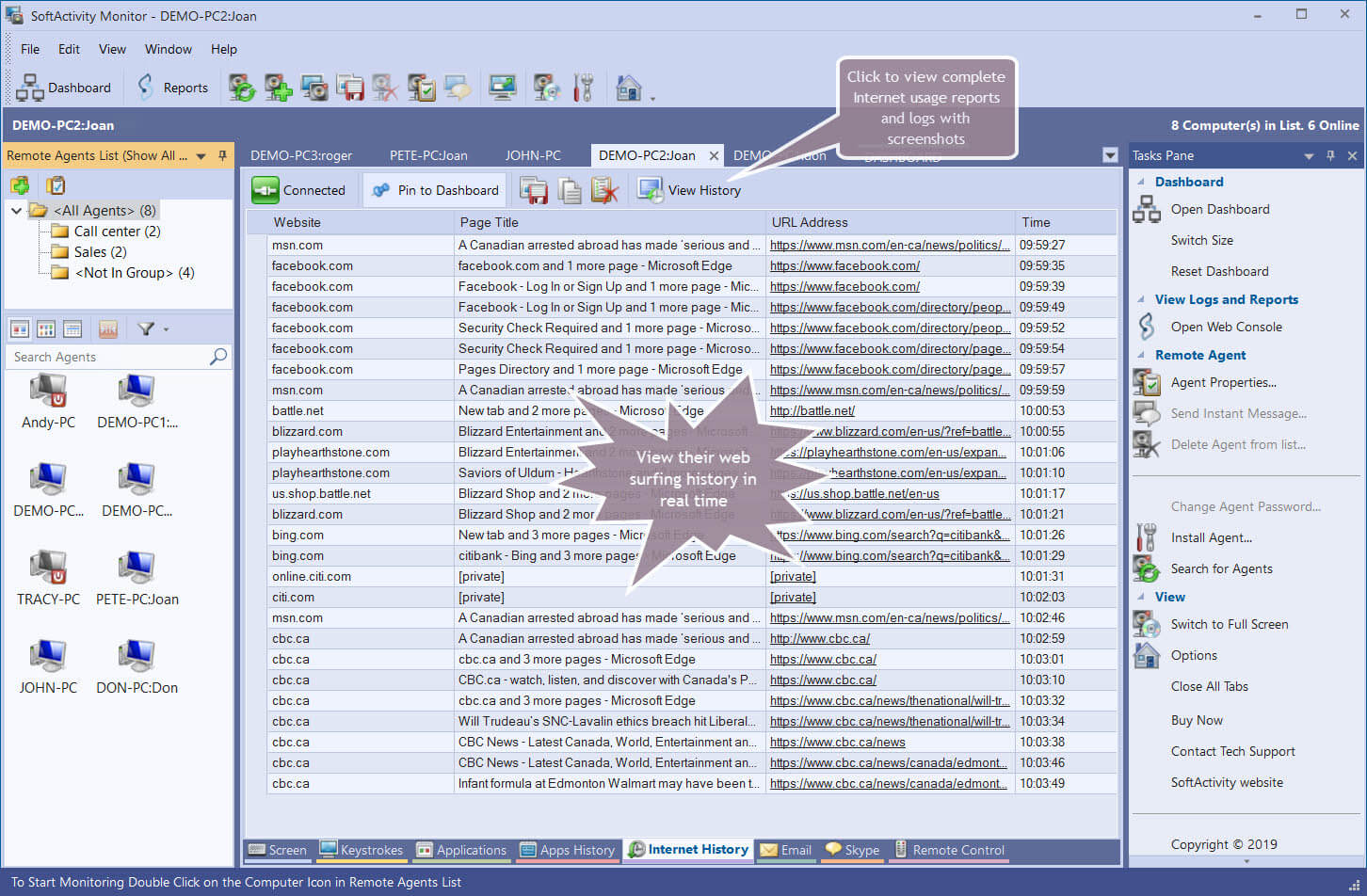
Webpage Tracking
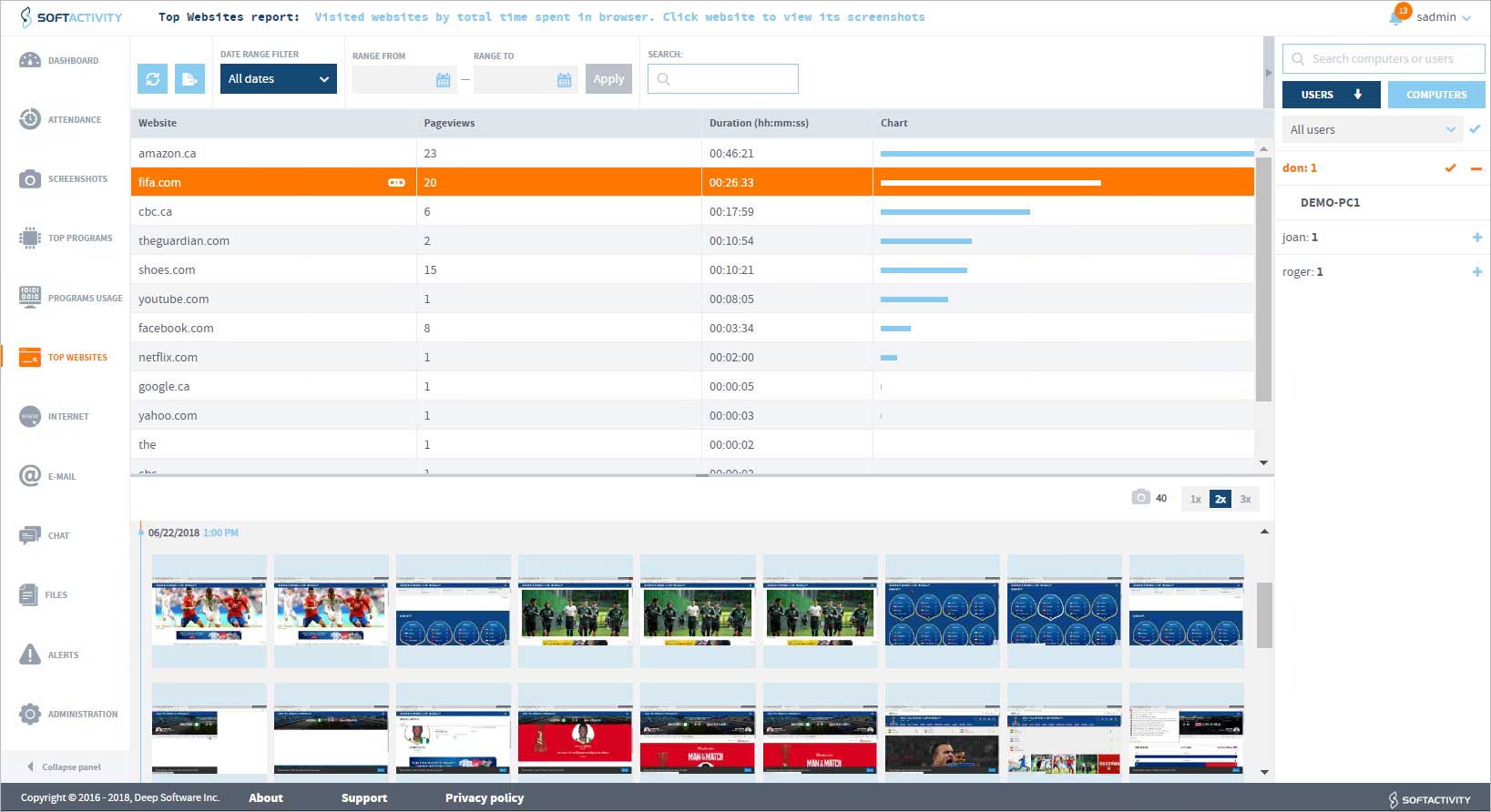
Webpage and IP tracking is the most common type of tracking performed by employee monitoring software. The software will store all the URLs visited on a browser of a user computer, even if the website was visited while in Incognito mode or if the history was cleared. A Top Website report can show you the total amount of time that an employee has spent on a webpage. You can identify the date and time a website was accessed and set up banned or flagged web pages. If a flagged page is visited the admin will be alerted.
Real-Time Application Tracker
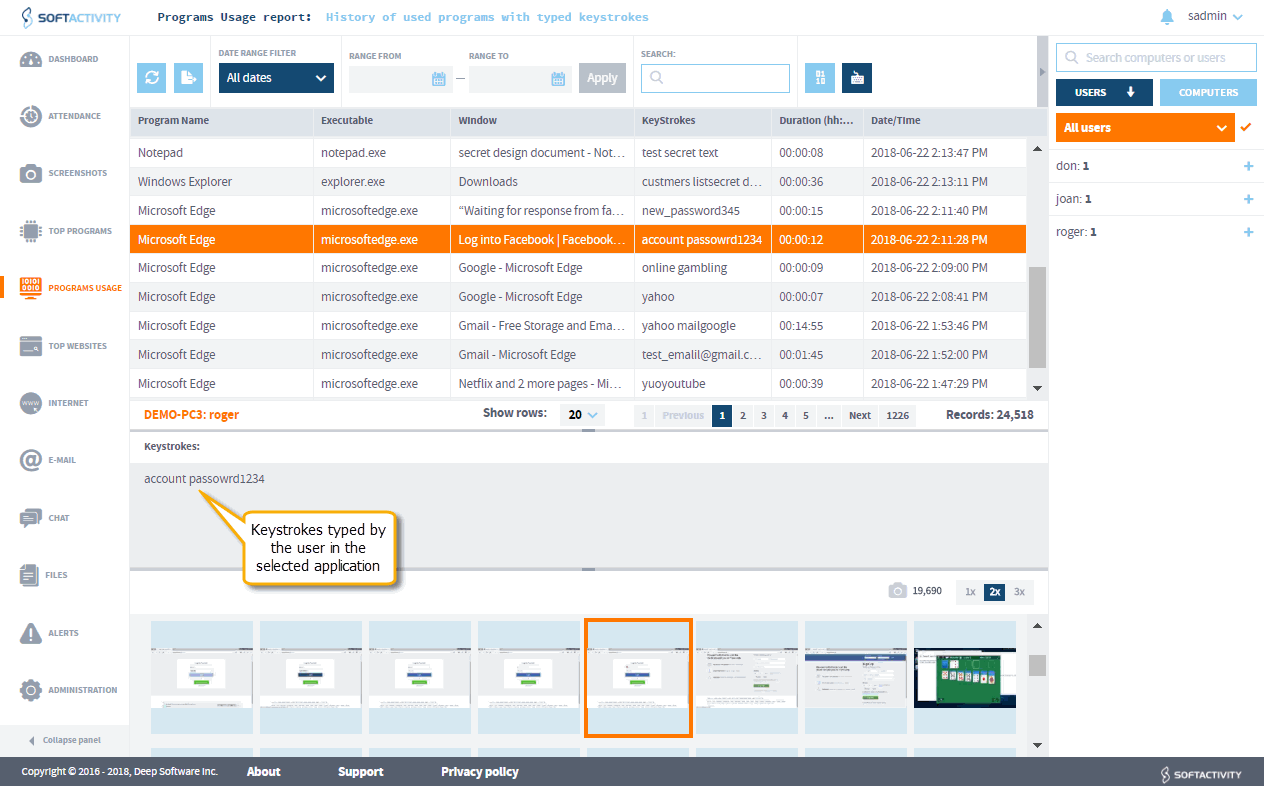
In addition to webpage tracking, you can track application use to monitor an employee’s productivity. This works best with installed software, but keystroke recording will identify accessed apps as well. Application monitoring works best with regular screenshots enabled so you can see what activities are done. This can stop users from wasting time or moving sensitive data. It can also log local and remote sessions, such as RDP, TeamViewer, and LogmeIn.
Live chat monitoring

Similar to application monitoring is live chat monitoring. Track all messenger and social media communication done on a user computer. Live chat activity monitoring should also screenshot the activity, time and date stamp when the conversation took place, who the conversation was with, and the content of the chat.
Email monitoring
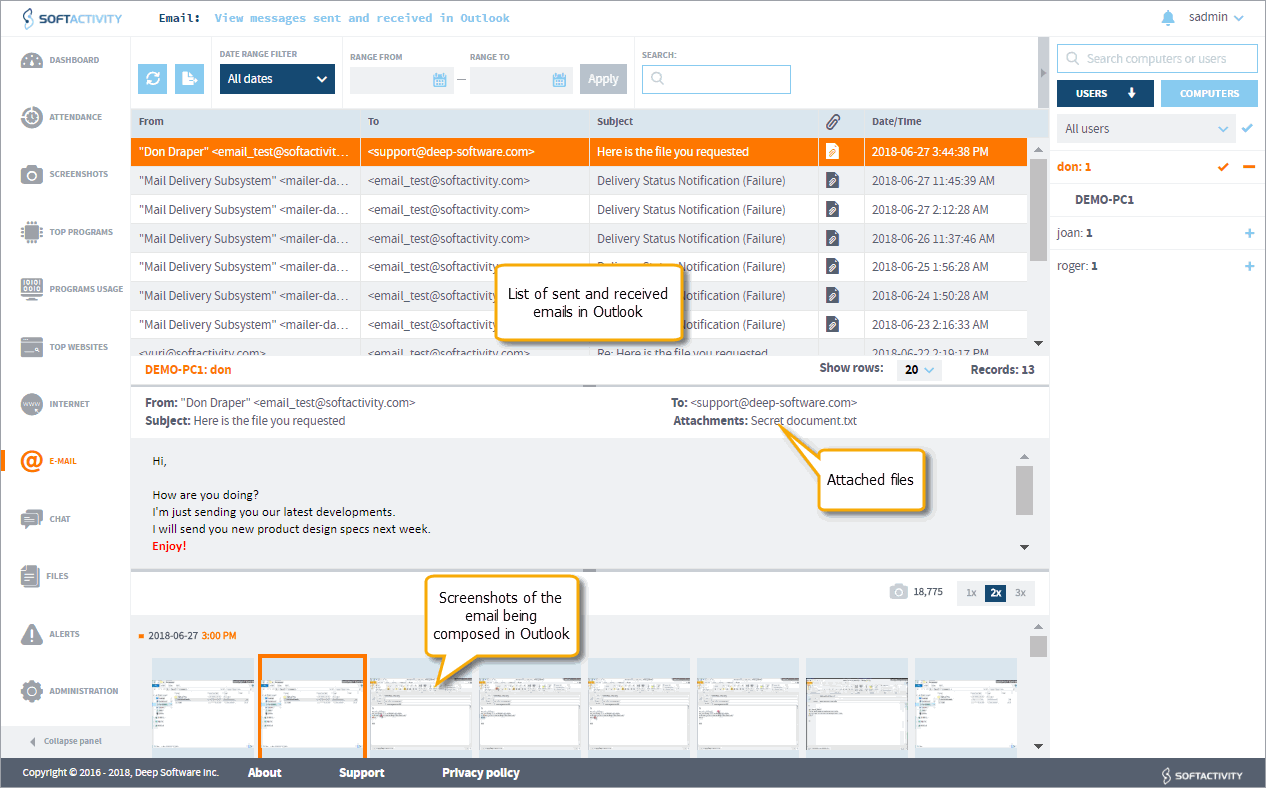
In essence, email monitoring is making a copy of all emails that go in and out on a computer. Admins can even view attachments. Keep track of the information that employees share to flag insider threats or potentially weak firewalls.
Keystroke Logger

A keystroke logger logs and categorizes every key that a user hits during any given session. The keystroke is logged regardless of the application or website being used. A keystroke logger will date and timestamp all keystrokes along with the application that was being used. The keylogger technology used by SoftActivity supports all international characters. An alert can be sent to the admin when users type particular trigger words.
Removable device monitoring
Removable devices like smartphones and tablets generally connect to a business network. However, without an installed monitoring software on that mobile device, it can be difficult to track mobile apps or data transfers. With the right employee monitoring software, you can monitor which devices were connected to the network and the types of files that were downloaded or uploaded to your network.
Screenshots
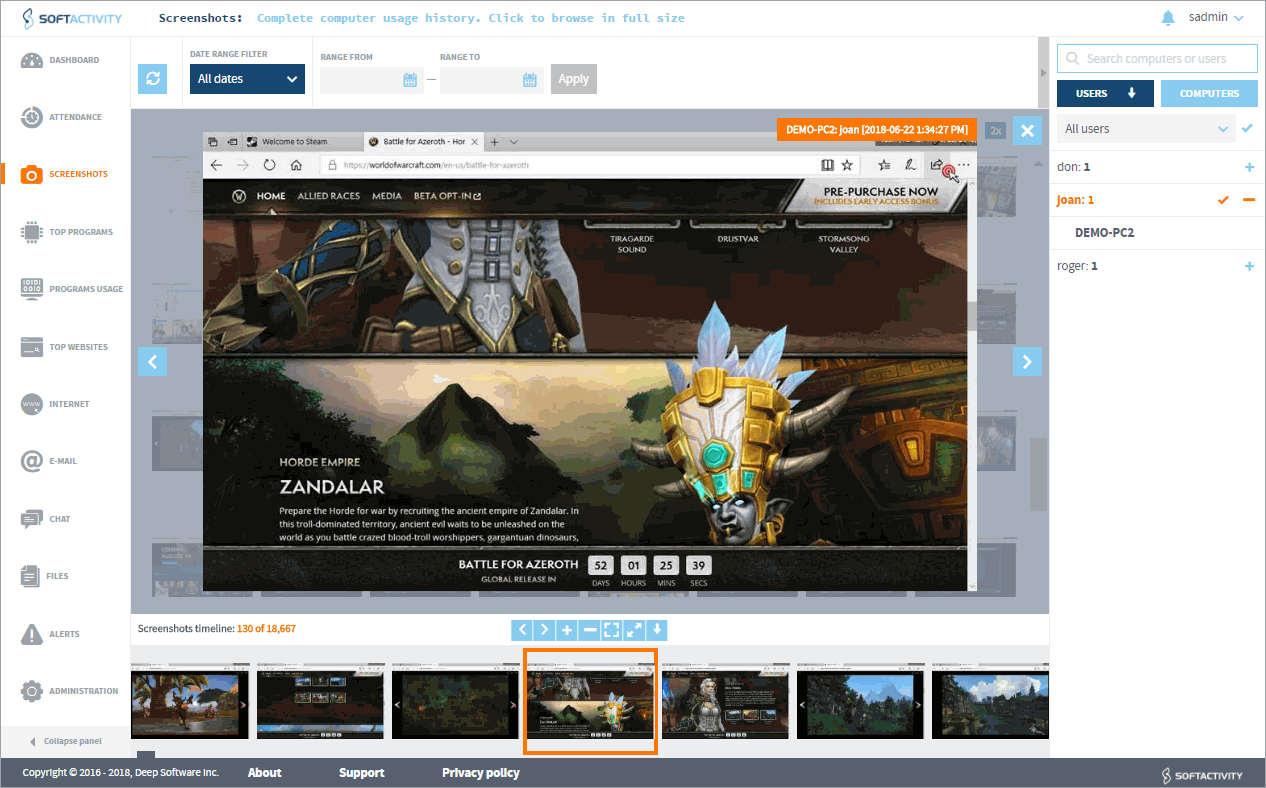
It will be useful to invest in screenshot capability. Screen capability is a feature of employee monitoring software that regularly or selectively takes a snapshot of a computer screen. The employee can be alerted to the screenshots or they can remain hidden. Screenshot applications used, periodic computer use, or every time an employee accesses a certain application. Screenshots are particularly effective at boosting productivity and keep employees off social media.
Webcam access
Depending on your level of security, webcam access may be useful for your monitoring needs. This allows admins to access the webcam view to verify identity, a nifty feature for remote workers to ensure that they are working during work hours.
Critical Alerts
Effective employee tracking software will send instant alerts when a flagged website is accessed, or a user violated your company’s computer use policy. Critical alerts open up investigations in security incidents, flag high-risk employees, and keeps your team alerted to new network threats.
Security Incident Analysis
Request or create security reports that clearly identify where the security breach occurred or potential red-flags to keep top of mind. Perform analysis behind insider threat alerts, network breaches, or flagged network activity like uploading files to a USB or browsing a dangerous website. This can also alert your team to critical logistics or productivity issues.
Attendance Tracker

Your employee monitoring software can act as an attendance tracker. Quickly view all sessions to identify lapses in productivity and to check attendance. This attendance view can log the computer and user’s name, the date and time stamp, the session duration, the top programs and top websites used, keystrokes, the IP address for RDP sessions, and provide a screenshot timeline. Attendance tracking through a monitoring app is more efficient and accurate than self-reporting.
Third-Party Watch
Third-parties are a major reason for data breaches. Allowing third-parties, such as your vendors or partners, remote access to any of your company networks creates another potential beachhead. It can be difficult to monitor your extended network with several new remote access points. With a third-party reporting feature, you can monitor the type of network access a third-party has.
Ethical Insider Watch
You’ll want your internet monitoring software to still prevent an insider threat while also being HIPAA and PCI compliant. Only monitor critical employee behavior, like the transfer of sensitive intellectual property or valuable data.
Network and Admin Support
All activity monitoring reports should be viewable on the admin web console; the web console can be installed on-premise or in cloud, and accessible remotely. Admins should be able to search through computer logs, export computer usage reports (e.g., HTML, PDF, Excel), and create and create supervisor accounts for other managers in the company. Multiple managers can track computers depending on their department. Most internet monitoring software will support Workgroup or Active Directory infrastructure.
The SoftActivity Difference
Our employee monitoring software is a powerful solution to maintaining the security of your company and protecting your assets. Employee monitoring software with SoftActivity means that your security is housed on-premise so you don’t have to worry about your data being compromised. Comprehensive user reporting allows the admin to stay on top of network concerns right away.
Our solutions have increased employee efficiency and they protect against data leakage. SoftActivity is available as a perpetual license and we continue to support Windows clients and server operating systems. With over 15 years of proven experience, we know what your company needs to keep your data safe.
Related:
Employee Monitoring: An Expert Guide
Download your SoftActivity Free Trial now!