You may have heard the popular saying in computer security: “It is not IF, but when you get breached”. There are a lot of cybercriminals out there and every day they are looking to breach a company’s vulnerabilities.
Cyber-attacks are increasing and the weakest vector of compromise is the users in your network. Having an employee monitoring solution, like keylogger software, in place is a proactive way of limiting and protecting against insider threats.

What is a Keylogger?
A keylogger is a hardware device or a software application that runs silently on a computer and logs the keystrokes typed by a user on the keyboard.
Hardware keyloggers are usually small USB dongles that plug into the computer you want to be recorded. This type of hardware is OS independent. They can capture text typed on the keyboard as soon as the computer is turned on so you can capture computer sign-in passwords and keystrokes regardless of security software or firewalls. Hardware loggers generally only work with external keyboards and they will not record most laptop keyboards or when a user is typing in a non-Latin alphabet.
Hardware loggers can easily be used maliciously. If the user is unaware that their keystrokes are being captured and the operator has malintent, the information obtained about the user, the business of the user, and other sensitive data can be used as a form of ransomware or to infiltrate the company network.
Physical access to premises and computer equipment is usually required to install hardware loggers since it needs to be plugged into a USB or PS-2 port. Then the keyboard is connected to the keylogger device.
However, the keystroke logs from the hardware device can be accessed later through a remote Wi-Fi connection, or stored locally in a device’s flash memory.
In addition:
- Sniffers exist that can intercept radio signals from a wireless keyboard.
- Simple video camera can be used for surveillance on the keyboard.
- An overlay can be applied to the keyboard, which is often used for ATM hacking for catapulting PIN codes.
There is even advanced acoustic technology to remotely recognize which keys are being pressed.

Software keyloggers work similar to hardware loggers but they allow a lot more flexibility. Keylogger software can be installed and accessed through remote connections, which allows your IT department to access and control it from anywhere.
This type of monitoring software mainly tracks typed text, but it is usually adapted with additional features like screen recording, application, and internet tracking and encryption of the log. In addition it may record typed password, credit card numbers, text typed on a virtual keyboard, and in text messaging apps. There are software keyloggers that support mobile devices, and the ones that support desktop- and server-based operating systems.
It also allows much more malleability in what is tracked and what is not. Typically software keyloggers are privacy-centric and they will put restrictions on who can access recorded keystrokes.
Why keylogger software?

While key loggers cannot protect against all types of keyboard security breaches, using keylogger software is easier than installing and managing keylogger hardware.
Depending on the scale of your business, you may benefit from using keystroke monitoring software to more efficiently and accurately monitor user keystrokes and computer activity.
Keylogging software can drastically decrease the amount of work for your IT department. A keystroke logger can be installed through remote connections and its presence is invisible.
Some employee monitoring software products can also handle keystroke logging in addition to other security needs. In this sense, you can control the types of user activity you want to be recorded.
Some keystroke software can also identify external or embedded keyboards, mouse clicks, and the computer applications a user has interacted with. It can also capture specified user activity events and can present detailed reports through live or recorded feeds.
Here are some of the detailed features you can get with software-based keylogger:
- Record keystroke activity
- Record any websites visited as well as snapshots of the website
- Logs around instant messages and emails sent or received
- Applications opened by the user in a certain period of time
- Install remotely by company admins
The above are just a few features that you can expect from a keylogging tool.
You may be thinking that this type of oversight is extreme. However, consider that the average cost for a security breach is $2 million (even for small businesses) and that most breaches occur through insider threats. Using a monitoring software will save your company millions of dollars and the potential for being shut down because of a breach.
Below are a couple of use case examples that a keylogger could help prevent:
- A disgruntled employee copying source code or social security numbers and sending them out to their personal Google Drive
- Mediation during malware/phishing investigations; you can truly see what the user saw and compare it to the action that was taken on-site
- Sending emails externally that contain login credentials for an admin account on a management server
By utilizing this level of visibility and employee oversight, you are being proactive about securing your company’s sensitive information. Using employee monitoring technology, such as a keylogger, can protect your company’s digital and physical assets.
How do I get a keylogger for my company?
There are several companies out there that provide keystroke recording software for businesses. An intuitive solution would be from SoftActivity. SoftActivity can provide both user activity monitoring and Terminal Server monitoring.
SoftActivity adopts a broad approach to monitoring user activities.
These include:
- Silent monitoring, not visible to users
- Secret recording visited websites
- User session and screen recording
- Keystroke logging
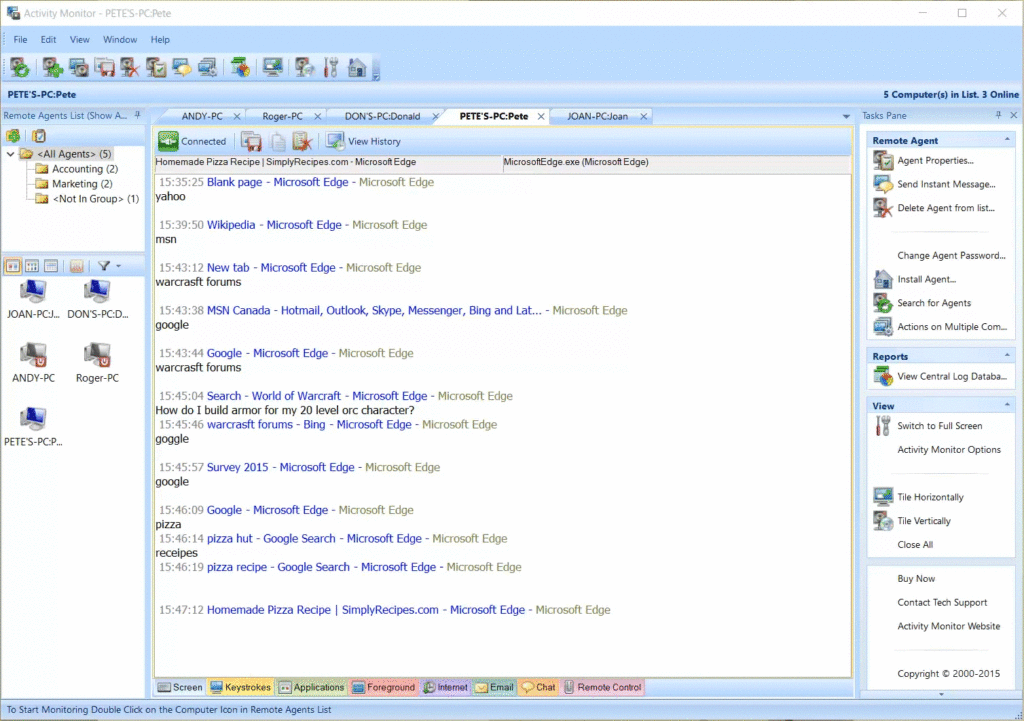
Below is an example of what it looks like to monitor a user’s keystrokes activity using SoftActivity Monitor. This is done in real-time and remotely.
(click the image to enlarge)
The Terminal Server monitoring solution from SoftActivity offers the ability to track user activity off-premises while also recording private user sessions and monitoring Internet activity. Our software has the following features so your company can easily transition to using keylogger software:
- Supports all Windows Operating System versions (as well as servers)
- Deploy Agent remotely and silently in your organization
- Data is securely stored on-premise
- Easy to understand GUI for viewing logs in a web browser
Protect your bottom line
Unfortunately, humans contribute to the bulk of mishaps when it comes to cyber incidents. Major cyber incidents can easily occur if your IT forgot to update a server or if an employee didn’t properly lock their computer.
When working in IT and networking, you always need to trust but verify. A great way to accomplish this guideline is to invest in a keylogger solution for your company.
Learn more about SoftActivity Monitor
By SoftActivity Team